Wireshark Cheat Sheet: Capture, Filter, and Shortcuts Guide
Wireshark Cheat Sheet Notes
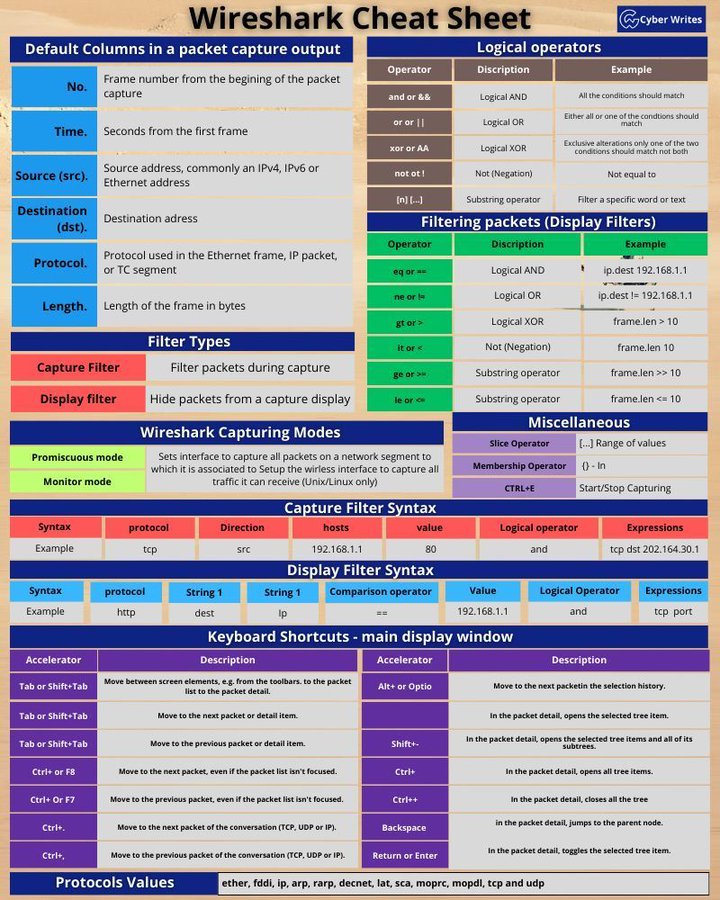
Default Columns in a Packet Capture Output
- No. :
- Frame number from the beginging of the packet capture.
- Helps to identify the specific frame within the entire capture sequence.
- Time:
- Seconds from the first frame.
- Useful for understanding the timing and sequence of network events.
- Source (src). :
- Source address, commonly an IPv4, IPv6 or Ethernet address.
- Identifies the sender of the packet.
- Destination (dst). :
- Destination address.
- Indicates the recipient of the packet.
- Protocol:
- Protocol used in the Ethernet frame, IP packet, or TC segment.
- Examples include HTTP, TCP, UDP, etc.
- Length:
- Length of the frame in bytes.
- Important for analyzing the size of the data being transmitted.
Logical Operators
| Operator | Description | Example |
|---|---|---|
| and && | Logical AND | All the conditions should match. |
| or | ||
| xor or AA | Logical XOR | Exclusive alterations only if the two conditions should match not both. |
| not ! | Not (Negation) | Not equal to. |
| [n....] | Substring operator | Filter a specific word or text. |
Filtering Packets (Display Filters)
| Operator | Description | Example |
|---|---|---|
| eq or == | Logical AND | ip.dest == 192.168.1.1 |
| ne or != | Logical OR | ip.dest != 192.168.1.1 |
| xor or ^ | Logical XOR | frame.len ^ 10 |
| gt or > | Greater operator | frame.len > 10 |
| lt or < | Less operator | frame.len < 10 |
| not or ! | Not (Negation) | |
| ge or >= | Substring operator | frame.len >= 10 |
| le or <= | Substring operator | frame.len <= 10 |
Filter Types
| Filter Type | Description |
|---|---|
| Capture Filter | Filter packets during capture. |
| Display Filter | Hide packets from a capture display. |
Wireshark Capturing Modes
- Promiscuous mode:
- Sets interface to capture all packets on a network segment to which it is associated.
- Helps in capturing all traffic regardless of destination.
- Monitor mode:
- Sets up the wireless interface to capture all traffic it can receive (Unix/Linux only).
- Useful for capturing wireless network traffic.
Capture Filter Syntax
- Syntax:
protocol Direction hosts value Logical operator Expressions - Example:
tcp src 192.168.1.1 80 and tcp dst 202.164.30.1 - Allows the specification of conditions to capture only relevant packets.
Display Filter Syntax
- Syntax:
protocol String 1 String 1 Comparison operator Value Logical Operator Expressions - Example:
http dest ip 192.168.1.1 and tcp.port - Used to filter packets for display based on various criteria.
Keyboard Shortcuts - Main Display Window
| Accelerator | Description |
|---|---|
| Tab or Shift+Tab | Move between screen elements, e.g., from the toolbars to the packet list. |
| Tab or Shift+Tab | Move to the next packet or detail item. |
| Tab or Shift+Tab | Move to the previous packet or detail item. |
| Ctrl+ or F8 | Move to the next packet, even if the packet list isn't focused. |
| Ctrl+< or F7 | Move to the previous packet, even if the packet list isn't focused. |
| Ctrl+= | Move to the next packet of the conversation (TCP, UDP, or IP). |
| Ctrl+- | Move to the previous packet of the conversation (TCP, UDP, or IP). |
| Alt+or Optio | Move to the next packet within the selection history. |
| Alt+Shift+ | In the packet detail, opens the selected tree item. |
| Shift+< | In the packet detail, closes the selected tree item and all of its children. |
| Ctrl+1 to Ctrl+4 | In the packet list, activates the 1st packet, the 2nd packet, etc. |
| Shift+- | In the packet list, deactivates the next line. |
| TAB | Move forward through items sequentially. |
| Ctrl+< | In the packet detail, collapses the selected tree. |
Protocol Values
- Including but not limited to:
etherfddiiparprarpdecnetlatscamoprcmopdltcpudp
Miscellaneous
- Slice Operator:
[...]- Range of values. - Membership Operator:
()- In. - CTRL+E: Start/Stop Capturing.
Remember, this cheat sheet summarises essential commands for efficient use and understanding of Wireshark, a powerful network protocol analyzer.
Reference:
www.comparitech.com
Wireshark Cheat Sheet – Commands, Captures, Filters & Shortcuts
www.stationx.net
Wireshark Cheat Sheet: All the Commands, Filters & Syntax - StationX
akhil.sh
Wireshark Cheat sheet | Tutorials - Akhil Personal Website