Magnum Certificate Management: Issues and Solutions
Notes on Magnum Certificate Generation
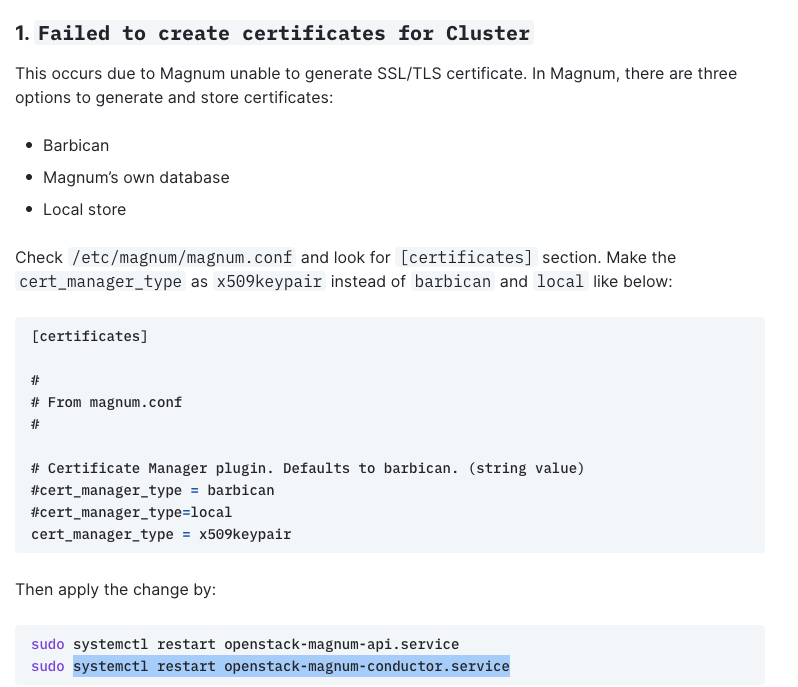
1. Issue: Failed to Create Certificates for Cluster
- Overview: This issue occurs when Magnum is unable to generate SSL/TLS certificates necessary for its operations. Proper certificate management is crucial for secure communications in cloud environments.
2. Options for Generating and Storing Certificates
-
Barbican:
- A secure store for secrets (API keys, passwords, certificates).
- Recommended for production environments due to its security features.
-
Magnum’s Own Database:
- Less secure than Barbican, as it stores certificates directly in the database.
- May suffice for testing or development purposes but not recommended for production.
-
Local Store:
- Utilizes local storage for certificates.
- Not secure for production as it can lead to exposure of sensitive data.
3. Configuration Steps
- Edit Configuration File:
- Locate the configuration file at
/etc/magnum/magnum.conf. - Look for the section labeled
[certificates]. - Change
cert_manager_typefrombarbicanorlocaltox509keypair. - This setting uses an x509 key pair for certificate management, which can enhance security.
- Locate the configuration file at
Example Configuration:
[certificates]# Certificate Manager plugin. Defaults to barbican.# cert_manager_type = barbican# cert_manager_type = localcert_manager_type = x509keypair
4. Restart Services
- After making the changes in the configuration file, it is essential to restart the necessary services for the changes to take effect.
sudo systemctl restart openstack-magnum-api.servicesudo systemctl restart openstack-magnum-conductor.service
- Thoughts: Restarting these services ensures that the new certificate management settings are applied, reducing potential downtime or security risks associated with unconfigured certificate handling.
Summary
Implementing the correct certificate management system within Magnum is vital for maintaining secure and reliable operations in a cloud environment. Proper configuration and service management will enhance the security posture of the deployment.
Reference:
docs.openstack.org
Magnum User Guide - OpenStack Documentation
docs.openstack.org
Magnum User Guide - OpenStack Docs
github.com
barbican_cert_manager.py - GitHub
Notes on Arkade and Kubernetes Setup
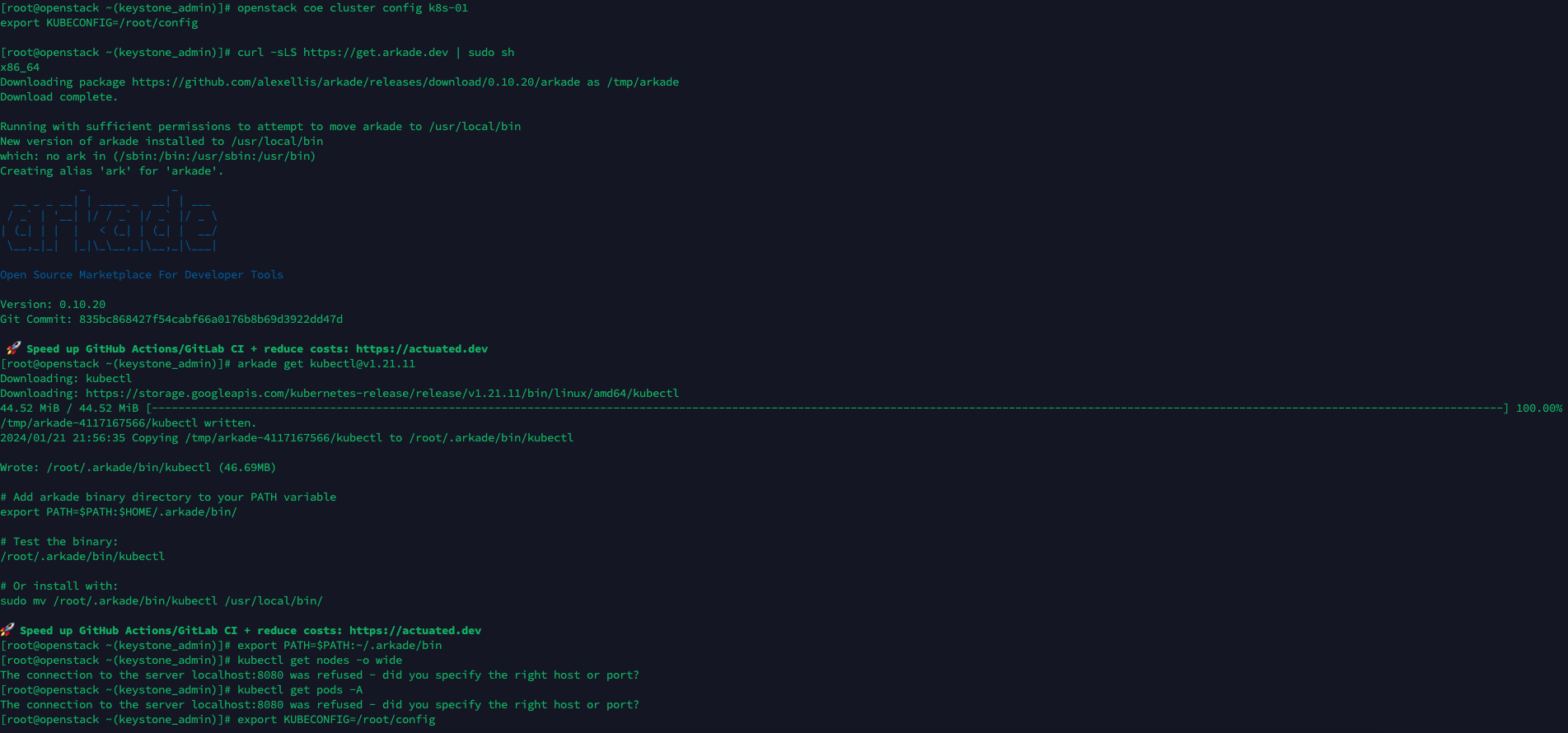
-
Installation of Arkade:
- The command
curl -sSL https://get.arkade.dev | sudo shdownloads and installs Arkade. - Thoughts: Arkade simplifies the installation of Kubernetes applications. It's vital for developers or operators needing to quickly deploy software on Kubernetes clusters.
- The command
-
Configuration for Kubernetes:
- The command
openstack coe cluster config k8s-01sets up necessary environment variables, specificallyKUBECONFIG, for accessing the Kubernetes cluster. - Additional Info: This step ensures that subsequent kubectl commands target the correct cluster context, crucial for successful cluster management.
- The command
-
Download of kubectl:
- The output shows the downloading of
kubectl, the command-line tool used to interact with Kubernetes clusters. It is downloaded from a Google Cloud storage location. - Thoughts: Having
kubectlis essential for managing Kubernetes resources effectively. It enables users to perform a wide array of operations from querying pod statuses to deploying applications.
- The output shows the downloading of
-
Path Configuration:
- Adding Arkade binary directory to the
PATHvariable withexport PATH=$PATH:~/.arkade/binallows the shell to recognize Arkade commands without specifying the complete path. - Tip: This makes it easier to run Arkade within any terminal session.
- Adding Arkade binary directory to the
-
Kubernetes Context Issues:
- The error message indicates a failure to connect to the Kubernetes server at
localhost:8080, suggesting that either the server isn't running or the wrong host/port is specified. - Recommendations: Ensure the Kubernetes cluster is up and running, and verify that the
KUBECONFIGpoints to the correct configuration file.
- The error message indicates a failure to connect to the Kubernetes server at
-
Commands to Test Configuration:
- The command
kubectl get nodes -o wideis used to retrieve details about the nodes in the cluster. This is a primary check to verify that the connection is working. - Idea: Regularly testing connections and configurations helps in proactively identifying and solving issues within cloud environments.
- The command
Summary of Key Outputs
| Command | Description |
|---|---|
| `curl -sSL https://get.arkade.dev | sudo sh` |
openstack coe cluster config k8s-01 | Sets KUBECONFIG for cluster access. |
export PATH=$PATH:~/.arkade/bin | Updates shell PATH to include Arkade commands. |
kubectl get nodes -o wide | Retrieves node details to verify connectivity to the cluster. |
Connection Error: did you specify the right host or port? | Indicates potential misconfiguration or server unavailability. |