PGP: Understanding Encryption, Key Management, and Trust Model
Data and Information Security - PGP

Decrypting the Message
-
Receiver's Private Key Retrieval
- Thought: This is crucial for ensuring that only the intended recipient can access the encrypted message.
- Explanation: PGP retrieves the receiver's private key from the private-key ring using the Key ID from the session key.
-
Passphrase Prompt
- Thought: Security hinges on user awareness and responsibility to maintain their passphrase.
- Explanation: The PGP prompts the user for the passphrase to recover the private key, reinforcing the importance of strong, secure passwords.
-
Session Key Recovery
- Thought: This key is fundamental for decrypting the actual message content.
- Explanation: Once the private key is retrieved, PGP recovers the session key and uses it to decrypt the message.
Authenticating the Message
-
Sender's Public Key Retrieval
- Thought: Authenticity checks help prevent impersonation and ensure message integrity.
- Explanation: PGP retrieves the sender’s public key using the Key ID from the signature key component of the message.
-
Transmitted Message Digest Recovery
- Thought: Message digests provide a fingerprint of the message.
- Explanation: PGP recovers the transmitted message digest to perform the integrity check.
-
Message Digest Comparison
- Thought: This step confirms that the message has not been altered during transmission.
- Explanation: The computed digest for the received message is compared to the transmitted digest to authenticate the message.
PGP Key Management
PGP uses four types of keys:
| Key Type | Description |
|---|---|
| 1. One-time session symmetric keys | Used once and generated for each new message. |
| 2. Public keys | Used in asymmetric encryption. |
| 3. Private keys | Also used in asymmetric encryption. |
| 4. Passphrase-based keys | Used to protect private keys. |
Key Management Insights
- One-time Session Symmetric Keys: These improve security by ensuring that keys are not reused, which could be susceptible to attacks.
- Public and Private Key Pair: This drives the asymmetric encryption process, allowing for secure communications without the need to share a common key secretively.
- Passphrase-based Keys: These add an additional layer of security by protecting private keys from unauthorized access.
Session Key Generation
- Key Size Dependence: The size of the session key varies based on the chosen encryption algorithm (e.g., CAST-128: 128 bits; 3DES: 168 bits).
- Generating New Keys: Utilizes user keystrokes and timing to generate new bits from a previous session key, enhancing uniqueness and security.
Importance of Session Key Generation
- User Involvement: By integrating keystroke timing, PGP ensures that even if an attacker has access to previous keys, they cannot predict future keys easily.
- Adaptive Security: This dynamic generation of keys makes PGP resilient against various types of cryptographic attacks.
Extended readings:
Public/Private Key Generation Notes

RSA Key Generation
-
Odd Number n: For generating RSA keys, n should be an odd number and sufficient size (usually > 200 bits).
- Explanation: Odd numbers are preferred because even numbers (other than 2) are not prime, simplifying the selection process for primality.
-
Finding Prime Numbers: If n isn't prime, a new random number is chosen and checked again until a prime is found.
- Idea: This iterative process ensures that the keys are secure and reliable, as prime numbers are fundamental in cryptography.
-
Performance Consideration: The search for prime numbers can be computationally expensive but typically occurs infrequently.
- Additional Information: Optimizations exist to reduce the search space, such as excluding even numbers.
Encrypting the Private Key
-
User-Supplied Passphrase: The private key is encrypted using a passphrase that the user provides.
- Thoughts: This adds an extra layer of security; even if someone gains access to the encrypted private key, they cannot use it without the passphrase.
-
Hash Generation: A hash code is created from the passphrase using SHA-1, producing a 160-bit hash.
- Explanation: Hashing the passphrase ensures that the actual passphrase is not stored, improving security.
-
Encryption Algorithm: The private key is encrypted with CAST-128 using 128 bits of the hash.
- Idea: This uses a symmetric encryption method, offering efficient encryption and decryption processes.
Key Management
-
Session Keys: In PGP (Pretty Good Privacy), session keys and passphrase-based keys are generated dynamically, used once, and then discarded.
- Additional Information: This practice minimizes the risk of key compromise and ensures session security.
-
Persistent Public and Private Keys: Public and private keys must be managed over time, as they are persistent and need preservation.
- Thoughts: Proper key management policies are essential for maintaining the integrity of encrypted communications.
Managing Key Pairs
-
Identifying Public Keys: Given that users can have multiple public/private key pairs, it’s important to know which public key was used for encryption.
- Possible Solutions:
- Send the public key with the message: This method can be inefficient as public keys can become large.
- Unique ID Association: Each key pair could be associated with a unique ID to streamline identification.
- Consideration: This requires a trusted mapping of IDs to keys to be known by all participants.
- Possible Solutions:
-
Generate a Unique ID: For a given user, an ID can be generated using the least significant 64 bits of the key.
- Explanation: This simplifies the process of identifying keys without the need to transfer large keys, facilitating smoother communication and encryption.
Extended readings:
Data and Information Security: Key Rings

Key Rings Overview
- Purpose: Key rings are used in cryptographic systems to manage public/private key pairs for secure communication.
- Components:
- Private-Key Ring: Contains the user's private keys.
- Public-Key Ring: Contains the public keys of other users.
Private Key Ring
| Field | Description |
|---|---|
| Timestamp | The date/time when the key pair was generated. |
| Key ID | 64 least significant digits of the public key. |
| Public Key | The public portion of the key, which can be shared with others. |
| Private Key | The private portion of the key, encrypted using a passphrase. |
| User ID | Typically the user’s E-mail address; may differ for different key pairs. |
Thoughts:
- Security: The use of passphrases to encrypt the private key is crucial for maintaining confidentiality.
- User Identification: The User ID helps in associating keys with specific individuals, making key management simpler.
Public Key Ring
| Field | Description |
|---|---|
| Timestamp | The date/time when the entry was created. |
| Key ID | 64 least significant digits of this entry. |
| Public Key | The public key for the corresponding entry. |
| User ID | Identifier for the owner of this key; multiple IDs can be associated. |
Thoughts:
- Key Sharing: The public key can be shared with anyone and is essential for encrypted communication.
- Indexing: Public keys can be indexed by User ID or Key ID, which enhances retrieval efficiency.
Retrieving a Private Key
- Decryption Requirement: PGP must decrypt the private key when needed for decryption.
- Process:
- PGP retrieves the receiver’s encrypted private key from the private-key ring using the Key ID.
- The user is prompted for the passphrase to access the unencrypted private key.
- Once the passphrase is verified, PGP recovers the session key and decrypts the message.
Thoughts:
- Reliability of Process: The accuracy of this process is crucial for ensuring secure communication.
- User Interaction: The necessity for a passphrase ensures that even if someone gains access to the encrypted key, they cannot use it without the passphrase, adding another layer of security.
Extended readings:
E-MAIL AND IP SECURITY

Validity of Public Key
- Each public key in a user's key ring has a Key Legitimacy field.
- This indicates the extent to which PGP trusts the key.
- Trust is important for ensuring secure communications and preventing unauthorized access.
Revoking Public Keys
- A user may want to revoke a public key for several reasons:
- Compromise is suspected: If a key might have been exposed or misused, it's critical to revoke it to protect communications.
- Limit the period of use of the key: Sometimes, keys are only intended for temporary use, such as for a specific project or duration.
- The owner will issue a signed key revocation certificate.
- This certificate should be communicated to recipients to update their public-key rings.
PGP Trust Model
- The PGP trust model helps establish the level of trust between users regarding their public keys.
- This model is crucial for the authenticity and integrity of encrypted communications.
Web of Trust
- The trust model is based on a web of trust:
- Users establish trust relationships with others they know.
- When a user creates a public key, they sign it with their private key and share it.
- Other users can verify the public key and sign it as well, which builds a chain of trust.
Authenticity and Integrity
- When an encrypted message is received, the PGP software verifies its authenticity using the sender's public key.
- If the key is trusted and the message verifies, the recipient can be confident of the sender's identity.
Challenges
- Managing trust relationships can be time-consuming and complex:
- Users must carefully manage their key rings.
- The model relies on the assumption that users are trustworthy.
- There is a risk of signing or distributing false keys, which can compromise security.
Overall, the PGP trust model is an essential aspect of secure communications, requiring diligent management and verification of keys to maintain trust within the network.
Extended readings:
PGP Trust Model Overview
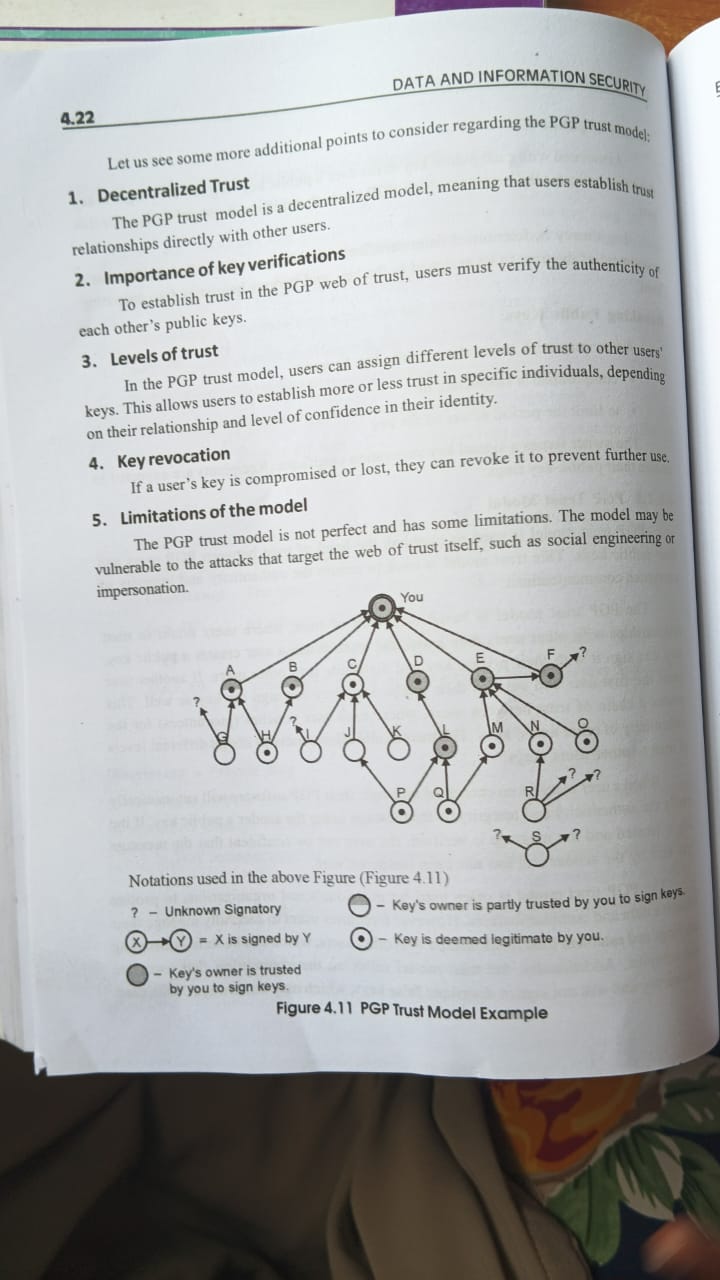
1. Decentralized Trust
- Explanation: The PGP trust model uses a decentralized approach, meaning users establish direct trust relationships with each other instead of relying on a central authority.
- Thought: This can enhance security by reducing single points of failure, but also requires users to be diligent in managing their connections and trust decisions.
2. Importance of Key Verifications
- Explanation: Users must verify the authenticity of each other’s public keys to build trust within the PGP web of trust.
- Thought: Verifying keys helps prevent impersonation attacks, highlighting the necessity of thorough verification processes through direct communication or established channels.
3. Levels of Trust
- Explanation: The system allows users to assign varying levels of trust to different keys. This flexibility is crucial for assessing relationships with other users.
- Thought: Users can choose to trust someone partially or fully based on their prior interactions, enhancing the granularity of trust management.
4. Key Revocation
- Explanation: Users can revoke their keys if compromised or lost, protecting themselves from unauthorized access.
- Thought: It is essential to have clear procedures in place for key revocation to quickly mitigate potential risks associated with compromised keys.
5. Limitations of the Model
- Explanation: The PGP trust model has inherent limitations, such as vulnerabilities to attacks targeting the web of trust, including social engineering.
- Thought: Understanding these limitations can help users implement additional security measures, like two-factor authentication or regular audits of trusted keys, to fortify their trust relationships.
Figure Notations
| Notation | Description |
|---|---|
| ? | Unknown Signatory |
| X | Key’s owner is trusted by you to sign keys |
| X - Y | X is signed by Y |
| ◯ | Key’s owner is partly trusted by you to sign keys |
| ◯ | Key is deemed legitimate by you |
Figure 4.11 PGP Trust Model Example
- This figure visually represents the relationships between different users and their keys, illustrating how trust can be established in a decentralized manner.
Extended readings: